So you have probably seen or heard about the announcement from Microsoft on the 14th of May. In summary:
“This July, Azure teams will begin rolling out additional tenant-level security measures to require multi-factor authentication (MFA). Establishing this security baseline at the tenant level puts in place additional security to protect your cloud investments and company”
More information about this subject can be found at the following links:
Announcement
FAQ
As I understand this, it will impact your whole organization, including Break Glass Accounts, Service Accounts, and Guests! Microsoft want you to migrate Service Accounts to Managed Identities or App Registrations, and to protect non-personal accounts like a Break Glass account with MFA Hardware (Yubikey for example). This is quite impactfull for all tenants, and even more when you look at the roll-out date starting in July!
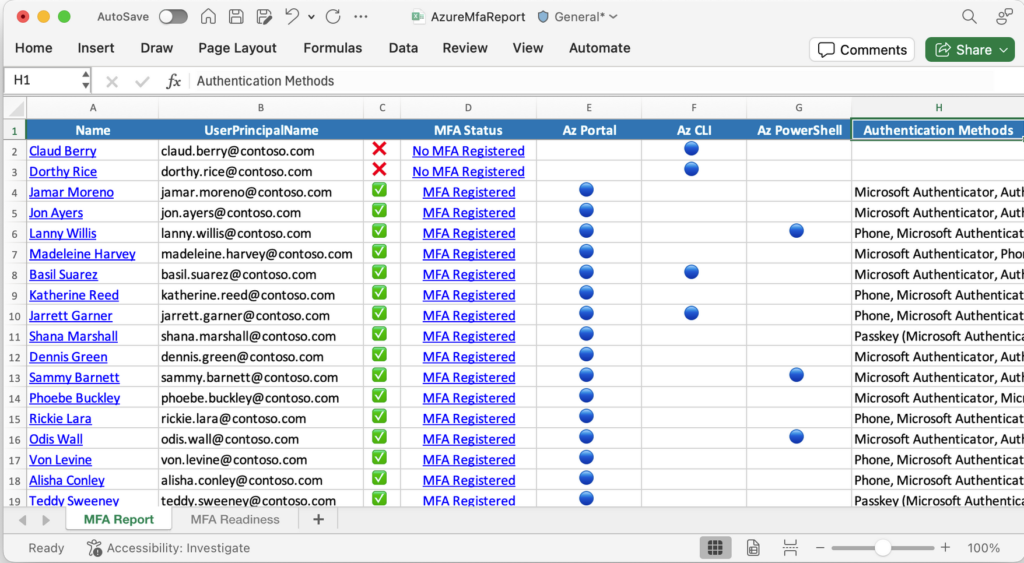
Microsoft has Developed a tool which will create a nice report to get an understanding of impacted admin users. I think this is strange because it only shows identities signing in to AZ CLI, AZ Powershell or the Azure Portal..
You can find the documentation about this at the following url: https://aka.ms/azmfa
Here you will find guidence on how to install the module and how to use it. The module will provide you with a report as shown below:
When looking on the Microsoft TechCommunity site we eye caught the following link:
So let’s find out what this is all about!
When clicking this link you will be guided to the following page:
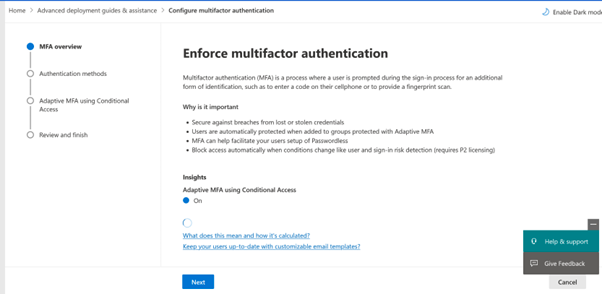
So it want to create Adaptive MFA Though Conditional Access, let’s explore some more and click next:
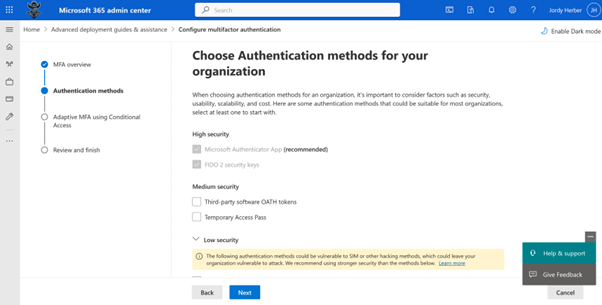
Alright, so here we are able to set the Authentication Methods that are being accepted in your policy (you still need to enable or disable them in Entra ID). Let’s select the defaults and click next again:
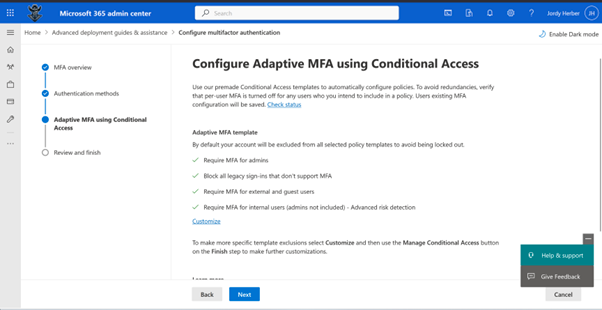
Okay, so it is really going to create some policies for us. for all users.. Let’s go on and review and finish!
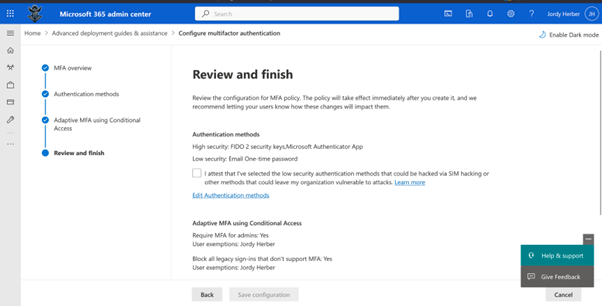
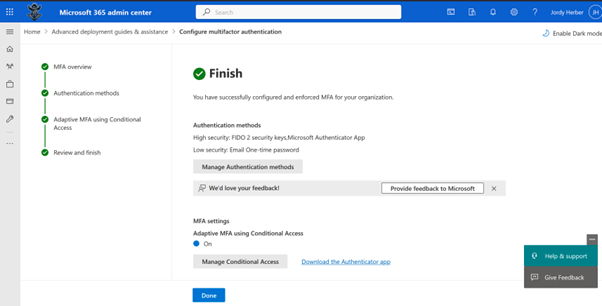
When this is complete, I went to the Conditional Acces portal and saw five newly reacted Conditional Access Policies:
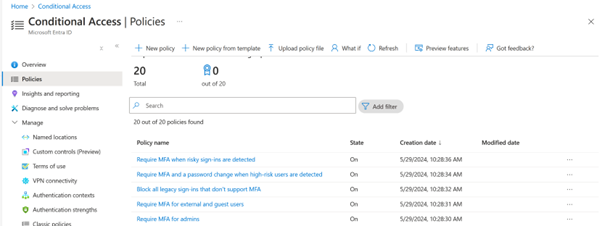
The good news: You can Disable the policies! For now…
Concluding.. It is still not very clear what is going to happen from July onwards, are we going to be able to set exclusions or disable the policies? Will the same policies be created automatically as from this wizard? Are they visible? Too much questions from my, and others for my liking.
Statement from Microsoft
So after some communication with Microsoft I got the message that the following comment is valid:
- Scope: All users signing into Azure portal, CLI, PowerShell, or Terraform to administrator Azure resources are within the scope of this enforcement.
- Impact on end users: Students, guest users and other end-users will only be affected if they are signing into Azure portal, CLI, PowerShell or Terraform to administrator Azure resources. This enforcement policy does not extend to apps, websites or services hosted on Azure. The authentication policy for those will still be controlled by the app, website or service owners.
- Exclusions: Service principals, managed identities, workload identities and similar token-based accounts used for automation are excluded. Microsoft is still gathering customer input for certain scenarios such as break-glass accounts and other special recovery processes.
- MFA Methods: All supported MFA methods are available for you to use.
- Exceptions: While there will be no opt-out, an exception process will be provided for cases where no workaround is available. Details for the exception process will be shared via official notifications.
- Timeline: Beginning July 2024, a gradual rollout of this enforcement for portal only will commence. Once we have completed the rollout for portal, a similar gradual rollout will start for CLI, PowerShell and Terraform. We understand the impact this enforcement could have on automated scripts using user identities and thus are prioritizing enforcement for Azure portal to provide additional time to adapt if needed.
- Communication: Microsoft will send detailed information and timelines through official emails and notifications with advanced notice to ensure customers are well informed and prepared. The purpose of this blog post was to generate awareness about this upcoming change and help you prepare for transition to multi factor authentication.
Actions
Summarizing all of the above:
- MFA will be enabled for all users with privileged roles, or have access to the Azure Portal so not for all users
- I suggest creating a report with the tool from aka.ms/azmfa
- Please make sure you assess PIM enabled users which doesn’t have a permenant role (these will not show in the report 🙂 )
- Create an action plan for your privileged Service Accounts -> Migratie te Managed Identities or App Registrations
- Take action for your Break Glass Accounts, implement Fidokeys or something else!
Microsoft will release some additional documentation or instructions when the time is right, so for now there is no clue how this change will be implemented within your tenant 🙂